
rvlsoft - Fotolia
Managed service provider security: Bad clients put your business at risk
Speakers at MSPWorld 2018 sparked new discussions about MSP security, such as how companies need to avoid entanglement with customers' security lapses.
NEW ORLEANS -- Talk about managed service provider security, and the discussion typically focuses on protecting customers and their data.
But the conversation has expanded in a different direction: MSPs may need to protect themselves from their own customers. That insight was among the developments at MSPWorld 2018, an MSPAlliance event taking place this week. Speakers participating in a security panel discussion suggested the evolving regulatory environment and the potential for customers' employees to commit crimes on MSP-hosted servers should give the industry pause.
"We are now facing a future where the behavior of your customers can actually get you in trouble," said Charles Weaver, CEO at MSPAlliance in Chapel Hill, N.C.
The MSP involved in Hillary Clinton's private email server controversy is a very public example of how service providers can become entangled in legal issues surrounding their customers' actions.
In addition, Robert Scott, managing partner of Scott & Scott LLP, a law practice based in Southlake, Texas, noted the possibility for a customer's employee to distribute child pornography on an MSP's server, adding that service providers could be responsible for crimes committed using their hardware.
A customer's action, or inaction, with regard to security is causing MSPs to avoid taking on some clients. John Burgess, co-founder and president of Mainstream Technologies, an MSP and hosting solutions provider based in Little Rock, Ark., said he looks to achieve alignment between the MSP's security philosophy and that of its customers.
"We spend a lot of time around our shop talking about alignment ... and use that as a measuring stick," he said.
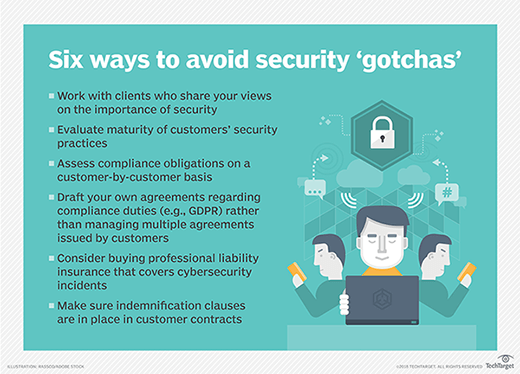
Does the prospective customer share Mainstream Technologies' vision for the role security should play in business? Is its coachable? Those are the types of questions the company asks, Burgess noted.
"If the customer is passionate about security, that is going to be a better customer for us to service," he said.
In general, the MSP has "moved our floor up" in recent years with respect to the security maturity level of the customers with which it works. Other firms have chosen to target somewhat larger customers with their managed service provider security offerings, noting small companies may not wish to purchase penetration testing or around-the-clock monitoring services.
Should you call the FBI?
An organization that has experienced a data breach should call the FBI, according to Brent Watkins, founder and CEO of GlobalSec Partners, a cybersecurity consulting firm in Las Vegas.
"I think it is very smart to call the FBI," he said. Watkins, who is a retired FBI special agent, said FBI agents assessing a breach ask questions that can help the organization solve its immediate problem and prevent it from happening again. And because agents may have seen a given type of intrusion before, they can provide advice, for example, on how to locate certain types of malware.
John Burgess, co-founder and president of Mainstream Technologies, said his MSP firm notifies the FBI as a service on behalf of its customers -- provided the customer experiencing a breach approves of such notification.
Shifting risk balance in managed service provider security
 Charles Weaver
Charles Weaver
Customers may also try to unload more of their regulatory compliance burden on an MSP, establishing contractual requirements beyond the scope of the regulation, Scott said.
He said the European Union's Global Data Protection Regulation (GDPR) is ripe for that sort of activity. GDPR, which goes into effect in May 2018, has implications for channel partners. That's particularly the case for service providers classified under the regulation as data processors -- that is, companies that handle the personally identifiable information of EU citizens.
Scott said he expects to see companies issue GDPR agreements that reach beyond the regulations' scope and shift the balance of risk toward the MSP. He said MSPs will find it difficult managing multiple, differing GDPR addendums from myriad clients. He suggested MSPs develop their own GDPR agreements instead.
"If clients say, 'We need a GDPR agreement,' send them yours," Scott suggested.
Focus on contract risk
In general, Scott highlighted the importance of focusing on customer contracts to assess the risk balance and conduct a customer-by-customer analysis of compliance obligations. He said MSPs that focus on a niche and understand their customers' regulatory environments better than they do will find success.
"For the customer, there is no distinction between IT and compliance," he said.

Scott also noted a potential down-the-road benefit from focusing on contracts. When an MSP goes up for sale, its No. 1 asset is customer contracts. The more risk a service provider can mitigate in customer contracts, the better its valuation, he said.






