managed security service provider (MSSP)
What is MSSP (managed security service provider)?
A managed security service provider (MSSP) is an information technology (IT) service provider that sells security services to businesses. The role of an MSSP is to help protect businesses from security threats, whether that means providing software and services that keep company data safe or building a network of security experts who can respond to attacks as they happen.
MSSPs provide cybersecurity monitoring and management, which may include virus and spam blocking, intrusion detection, firewalls and virtual private network (VPN) management. MSSPs also handle matters such as system changes, modifications and upgrades.
What are MSSPs used for?
Organizations may either outsource all or some aspects of their IT security functions to MSSPs. These companies offer a variety of services, such as continuous security monitoring, vulnerability risk assessment, threat intelligence and assessments, intrusion management, video surveillance and access control. MSSPs can also provide security recommendations and some level of continuous security, and they can develop policies to help protect a company's infrastructure.
MSSPs are an efficient and cost-effective way to protect your data and network from intrusions while reducing the complexity of the process. For example, hiring an in-house cybersecurity team can be more expensive than working with an MSSP. MSSPs can also help businesses save money on equipment and software tools.
Large enterprises typically benefit from MSSP services due to increased security threats. However, many small and medium-sized businesses (SMBs) can also benefit from MSSPs as security threats evolve. The demand for MSSPs is on the rise and the global managed security services market is forecasted to reach $46.4 billion by 2025.
There are six main categories of managed security services, including:
- on-site consulting;
- perimeter management of the client's network;
- product resale;
- managed security monitoring;
- penetration testing and vulnerability assessments; and
- compliance monitoring.
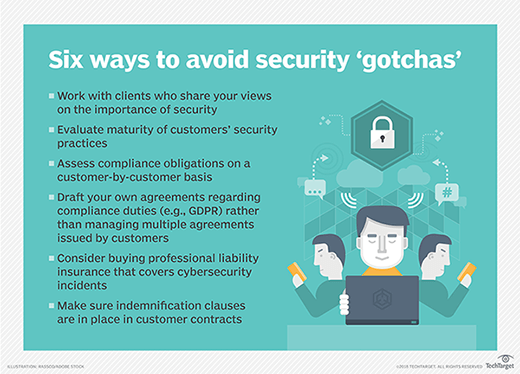
Categories of managed security services
On-site consulting
MSSP consulting is when an MSSP comes in and does a detailed security assessment of a company's network, identifying potential and real-world vulnerabilities. MSSP on-site consulting involves the MSSP finding the security holes and then helping the company fix them.
Perimeter management of the client's network
In the context of network security, a perimeter is the conceptual line that separates an organization's internal assets from the public ones. If a single enterprise network is used for security, then its perimeter would be the defenses that surround the network, protecting it from outside attack. The purpose of a perimeter is to limit access to sensitive data, usually by controlling who and what can get into the network. If you're an MSSP that's providing security to a large enterprise, a key part of your job is to ensure the organization's network perimeter is satisfactory and all the devices within it are well protected.
Product resale
Product resale is not a managed service but a revenue generator for MSSPs. An MSSP resells software, hardware and services to its clients. For example, an MSSP might have a catalogue of security devices, including intrusion prevention systems and firewalls, and its clients can choose from a variety of specialized offerings. The reseller might also provide technical support for the devices, perform penetration tests for security and perform security audits. The MSSP model arose when large companies dominated the market, each with its own set of security products. Resellers would then provide customers with a customized security solution made up of products from multiple vendors.
Managed security monitoring
Managed security monitoring is typically the first step in responding to a security incident report. It involves the regular day-to-day monitoring of security events such as user logins and permission changes, as well as investigation of such system events throughout the network.
Penetration testing and vulnerability assessments
Penetration testing and vulnerability assessments are methods for testing the security of an organization, usually its information and technology assets. Penetration testing is a form of ethical hacking that tries to break into computer systems to uncover vulnerabilities that hackers might exploit. In a penetration test, a team of trusted hackers attempts to hack into a company's computers or networks using the same tools and techniques that bad actors do. This simulated attack yields valuable information about how well the company defends itself against a real attack. Penetration testing is also called pen testing.
Compliance monitoring
Compliance monitoring is the process of checking an organization's compliance with policies and procedures for data security. Compliance monitoring usually involves an MSSP performing regular scans of your security devices and infrastructure. The MSSP will use the scan results to determine if any changes need to be made to your security software or infrastructure. This includes retrieving, storing and transmitting data in a secure and legally defensible manner. In order to ensure compliance, an organization is generally required to prove that it is complying with a variety of rules and regulations that govern electronic data storage and transmission.
What is the difference between an MSP and an MSSP?
A managed service provider (MSP) is a business that provides technology services to its clients using its own employees or contracting the work out to independent contractors. MSPs conduct a variety of services to their clients, including hardware and software maintenance, implementation and deployment.
A managed security service provider is a security-focused MSP that offers security-related services, such as network monitoring, security configuration and identity management.
How MSSPs have evolved
MSSPs have evolved in various ways. Some traditional service providers, noting the seemingly ever-increasing demand for internet security, have added managed security to their portfolios. Other traditional channel partners, such as a value-added reseller (VAR), will resell vendors' cloud-based security services.
Still other MSSPs have come into existence as brand new entities focused solely on cybersecurity offerings. Some industry observers have asserted that every channel company is a "security provider" to some extent, as nearly every aspect of a customer organization's operations features some cybersecurity component.
How to evaluate a managed security service provider
The five key areas to consider when evaluating an MSSP are:
- Expertise. Ensure an MSSP is staffed with experts in the field, including engineers and cybersecurity professionals.
- Services. Determine how well the MSSP's services align with an organization's needs and how well those needs can be met.
- Staff. MSSPs require a sufficient number of trained staff members in order to be readily available 24/7 to respond quickly to needs and emergencies.
- Security. Understand how an MSSP handles and maintains an organization's sensitive information.
- Budget. An organization must assess the pricing and service levels for an MSSP to determine if their budget can accommodate its services.
Evaluating a security service provider can be difficult because not every service offered by an MSSP provides value to a company. For example, an organization might not require mobile security if they have a small team. Determining the right MSSP for an environment requires examining each of these areas of evaluation to determine which is most important for a business.
Depending on the nature of a business, certain MSSPs also offer services to assist businesses in regulated industries. For example, some businesses are required to meet compliance requirements, such as the Health Insurance Portability and Accountability Act (HIPAA) or the European Union's General Data Protection Regulation (GDPR).
Managed security service provider list
Here is a list of some of the leading MSSPs on the market today:
- Anomalix
- AT&T
- Cipher
- Global IP Networks
- IBM
- Secureworks
- SecurityHQ
- Trustnet
- TSC Advantage
- Verizon






